Under the bonnet: Architecture overview
Dropbox is designed with multiple layers of protection, including secure data transfer, encryption, network configuration and application-level controls distributed across a scalable, secure infrastructure.
File infrastructure
Dropbox users can access files and folders at any time from a number of interfaces, including the desktop, web and mobile clients, or via third-party applications connected to Dropbox. Each has security settings and features that process and protect user data while ensuring ease of access. All of these clients connect to secure servers to provide access to files, allow file sharing with others and update linked devices when files are added, changed or deleted.
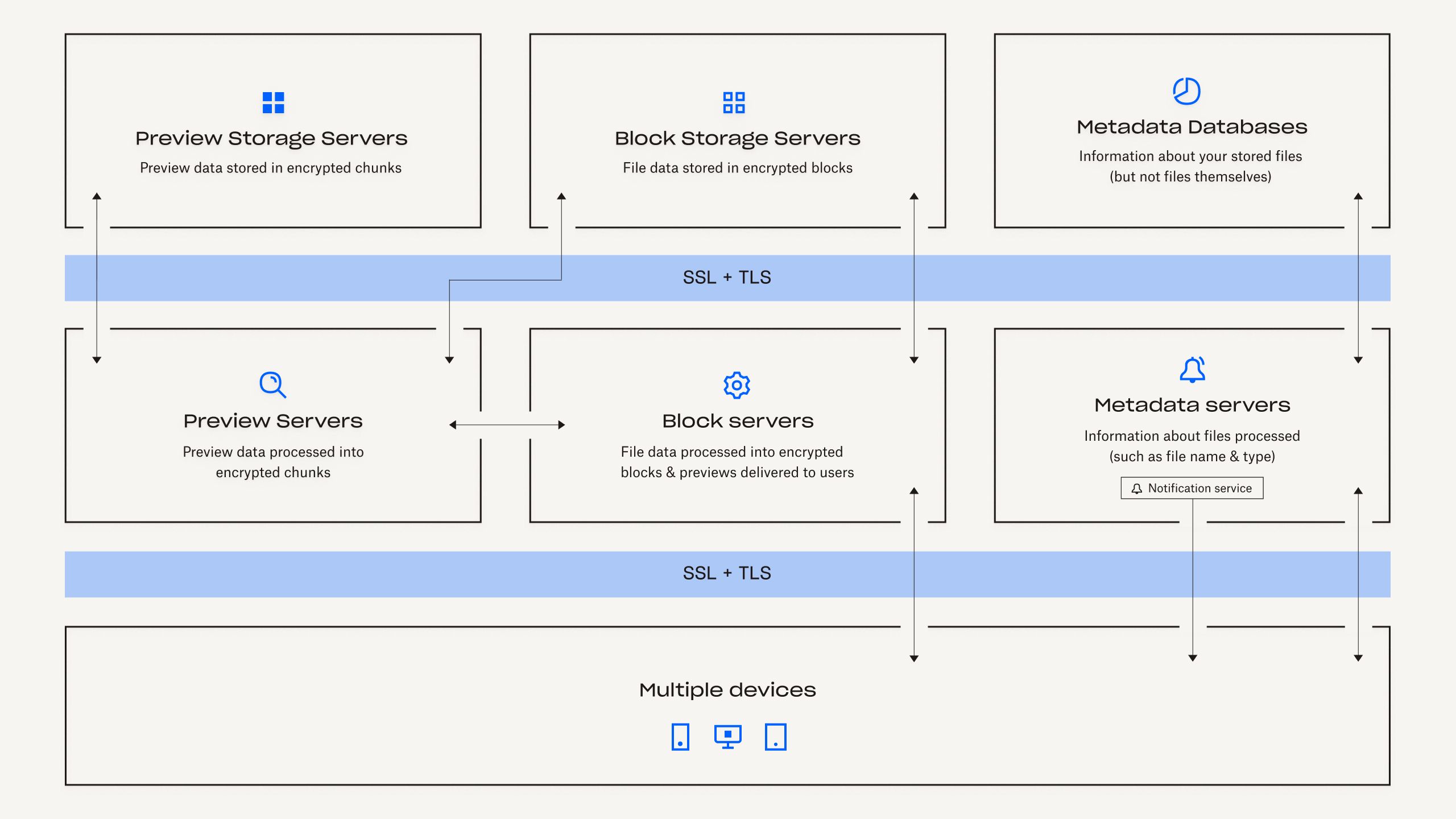
Our file infrastructure is comprised of the following components:
Metadata Servers
Certain basic information about user data, called metadata, is kept in its own discrete storage service and acts as an index for the data in users’ accounts.Metadata includes basic account and user information, like email address, name and device names.Metadata also includes basic information about files, including file names and types, that helps support features like version history, recovery and sync.
Metadata Databases
File metadata is stored in a MySQL-backed database service and is sharded and replicated as needed to meet performance and high availability requirements.
Block Servers
By design, Dropbox provides a unique security mechanism that goes beyond traditional encryption to protect user data.Block Servers process files from the Dropbox applications by splitting each into blocks, encrypting each file block using a strong cipher and synchronising only blocks that have been modified between revisions. When a Dropbox application detects a new file or changes to an existing file, the application notifies the Block Servers of the change, and new or modified file blocks are processed and transferred to the Block Storage Servers. In addition, Block Servers are used to deliver files and previews to users.
Block Storage Servers
The actual contents of users’ files are stored in encrypted blocks with the Block Storage Servers. The actual contents of users’ files are stored in encrypted blocks with the Block Storage Servers. Prior to transmission, the Dropbox client splits files into file blocks in preparation for the storage. The Block Storage Servers act as a Content-Addressable Storage (CAS) system, with each individual encrypted file block retrieved based on its hash value.
Previews Servers
The Previews Servers are responsible for producing previews of files. Previews are a rendering of a user’s file in a different file format that is more suited for fast display on an end user’s device. Previews Servers retrieve file blocks from the Block Storage Servers to generate previews. When a file preview is requested, the Previews Servers retrieve the cached preview from the Previews Storage Servers and transfer it to the Block Servers. Previews are ultimately served to users by Block Servers.
Previews Storage Servers
Cached previews are stored in an encrypted format in the Previews Storage Servers.
Notification Service
This is a separate service dedicated to monitoring whether changes have been made to Dropbox accounts. No file data or metadata is stored or transferred here. Each client establishes a long poll connection to the notification service and waits. When a change to any file in Dropbox takes place, the notification service signals a change to the relevant client(s) by closing the long poll connection. Closing the connection signals that the client must connect to the Metadata Servers securely to synchronise any changes.
Dropbox Paper infrastructure
Dropbox users can access Paper docs at any time from the web and mobile clients, or through third-party applications connected to the Dropbox Paper application. All of these clients connect to secure servers to provide access to Paper docs, allow doc sharing with others, and update linked devices when docs are added, changed or deleted.
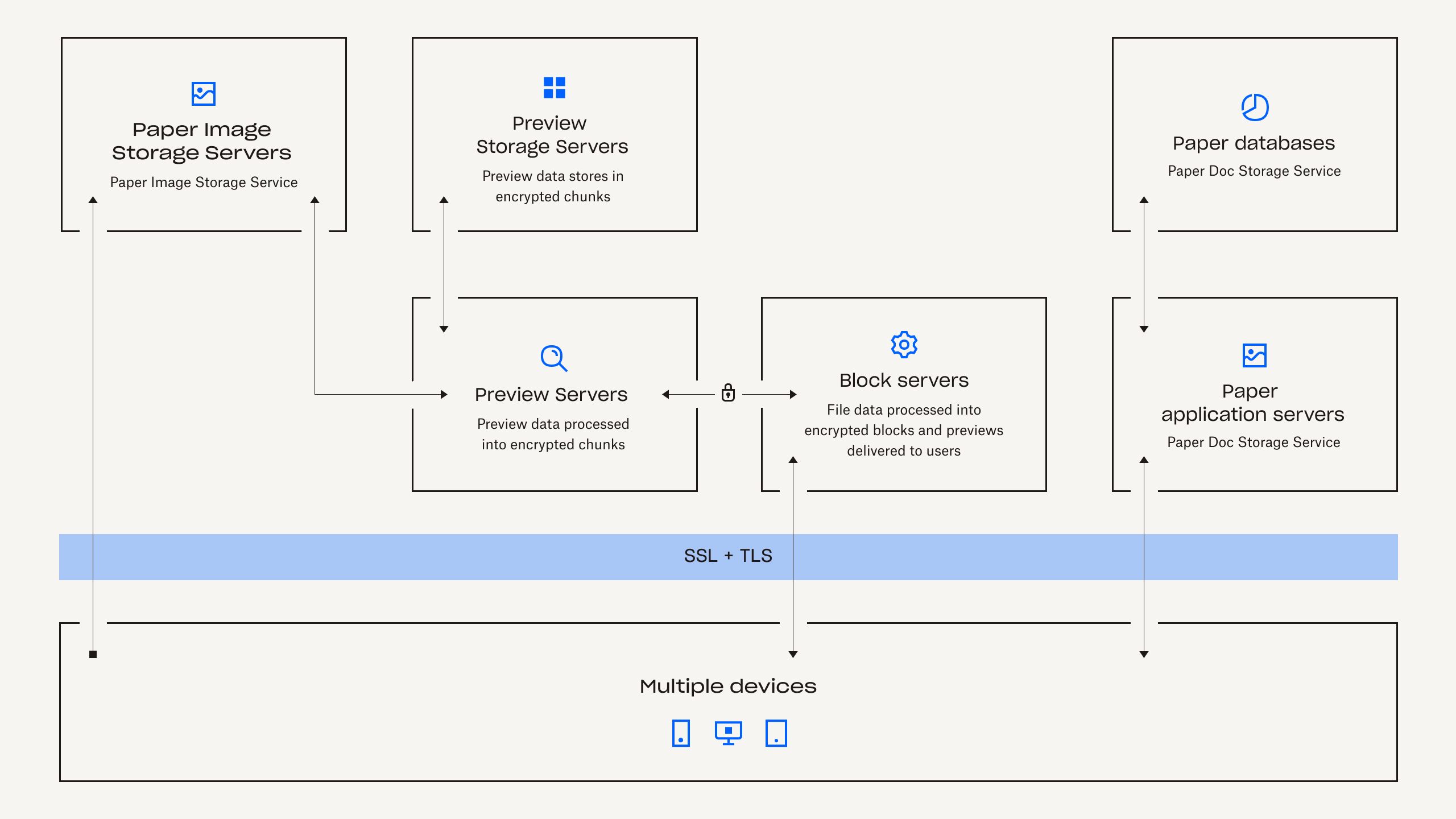
Dropbox Paper infrastructure is comprised of the following components:
Paper Application Servers
The Paper application servers process user requests, render the output of edited Paper docs back to the user and perform notification services. Paper application servers write user edits to the Paper databases, where they are placed in persistent storage. Communication sessions between the Paper application servers and Paper databases are encrypted using a strong cipher.
Paper Databases
The actual contents of users' Paper docs, as well as certain metadata about these Paper docs, are encrypted in persistent storage on the Paper databases. This includes information about a Paper doc (such as the title, shared membership and permissions, project and folder associations and other information), as well as content within the Paper doc itself, including comments and tasks. The Paper databases are sharded and replicated as needed to meet performance and high availability requirements.
Metadata servers
Paper uses the same metadata servers described in the Dropbox infrastructure diagram to process information about Paper docs, such as Paper doc file revision history and shared folder membership. Dropbox directly manages the metadata servers, which are located in third-party, co-located data centres.
Metadata Databases
Paper uses the same metadata databases described in the Dropbox infrastructure diagram to store information related to Paper docs, such as sharing, permissions and folder associations. Paper doc metadata is stored in a MySQL-backed database service and is sharded and replicated as needed to meet performance and high availability requirements.
Paper Image Storage Servers
Images uploaded to Paper docs are stored and encrypted at rest on the Paper image storage servers. Transmission of image data between the Paper application and Paper image storage servers occurs over an encrypted session.
Previews Servers
The previews servers produce previews both for images uploaded to Paper docs, as well as hyperlinks embedded within Paper docs. For images uploaded to Paper docs, the previews servers fetch image data stored in the Paper image storage servers via an encrypted channel. For hyperlinks embedded within Paper docs, previews servers fetch the image data and render a preview of the image using encryption as specified by the source link. Previews are ultimately served to users by block servers.
Previews Storage Servers
Previews storage servers Paper uses the same preview storage servers described in the Dropbox infrastructure diagram to store cached image previews. Cached preview chunks are stored in an encrypted format in the previews storage servers.
Both dedicated internal security teams and third-party security specialists protect these services through the identification and mitigation of risks and vulnerabilities. These groups conduct regular application, network, and other security testing and auditing to ensure the security of our back-end network. In addition, our responsible disclosure policy promotes the discovery and reporting of security vulnerabilities.
Data Centres
Dropbox corporate and production systems are housed at third-party subservice organisation data centres and managed service providers located in the United States. These third-party service providers are responsible for the physical, environmental and operational security controls at the boundaries of Dropbox infrastructure. Dropbox is responsible for the logical, network and application security of our infrastructure housed at third-party data centres.
Encryption
Dropbox files and Dropbox Paper docs at rest are encrypted using 256-bit Advanced Encryption Standard (AES). To protect data in transit between Dropbox apps (currently desktop, mobile, API, or web) and our servers, Dropbox uses Secure Sockets Layer (SSL)/Transport Layer Security (TLS) for data transfer, creating a secure tunnel protected by 128-bit or higher Advanced Encryption Standard (AES) encryption. Similarly, data in transit between a Paper client (mobile, API, or web) and the hosted services is encrypted via SSL/TLS.
Certificate Pinning
Dropbox uses certificate pinning on our file sync and share desktop and mobile clients. Certificate pinning is an extra check to ensure that our clients will only connect to servers with digital certificates from an authorised list of certificate authorities. We use it to guard against nation-state attackers in control of a rogue certificate authority, as well as to protect you from local malware that may be hijacking your connections.
Perfect forward secrecy
For endpoints we control (desktop and mobile) and modern browsers, we use strong ciphers and support perfect forward secrecy. By implementing perfect forward secrecy, we’ve made it so our certificate's private key can't be used to decrypt past Internet traffic. This adds extra protection to encrypted communications with Dropbox, essentially disconnecting each session from all previous sessions. Additionally, on the web, we flag all authentication cookies as secure and enable HTTP Strict Transport Security (HSTS).
Key Management
Dropbox’s key management infrastructure is designed with operational, technical and procedural security controls with very limited direct access to keys. Encryption key generation, exchange and storage is distributed for decentralised processing.
Dropbox manages file encryption on users' behalf to remove complexity, support advanced product features and enable strong cryptographic control. File encryption keys are created, stored and protected by production system infrastructure security controls and security policies. Access to production systems is restricted with unique SSH key pairs. Security policies and procedures require protection of SSH keys. An internal system manages the secure public key exchange process and private keys are stored securely.
Find more details about our control and visibility features in our Dropbox Security Whitepaper.